Cybersecurity Training for Your Business

ICE Consulting offers comprehensive cybersecurity training for your employees, users, and contractors. Our training services—taught by our IT experts—will help inform and educate your users about the latest cybersecurity vulnerabilities, policies, procedures, and trends.
We cover the following topics:
- Email and phishing
- Security at home network
- Information Security (InfoSec) policies and procedures
- Acceptable use of assets
- Password best practices
- Endpoint management
- Access control policy
- Least privilege
- Securely transmitting data
- Wireless network management
- Mobile device management
- IT asset and risk management
- Business continuity policy

Here are some examples of what you will learn
Information Security Policies
Why are Information Security Policies so important? They can help protect your business in these ways:
InfoSec policies govern how sensitive company information is handled
As security threats have been worsening, the biotech industry is increasingly targeted
Your company has created these InfoSec policies, which will substantially mitigate cybersecurity risks if properly followed
Email and Phishing—the #1 Threat You Face Today
According to a 2021 Data Breach Investigations Report (DBIR), Verizon Enterprise found phishing to be one of the most prevalent action varieties for the data breaches it analyzed. Its researchers specifically observed phishing in more than a third (36%) of breaches. That’s up from 22% a year earlier.
Phishing emails and text messages might make it past your filters because they convey a sense of urgency, may appear to come from an executive, or ask you to take action that you weren’t expecting. We tell our clients to report any suspicious emails to IT before clicking on links or replying. Always maintain a healthy level of skepticism.
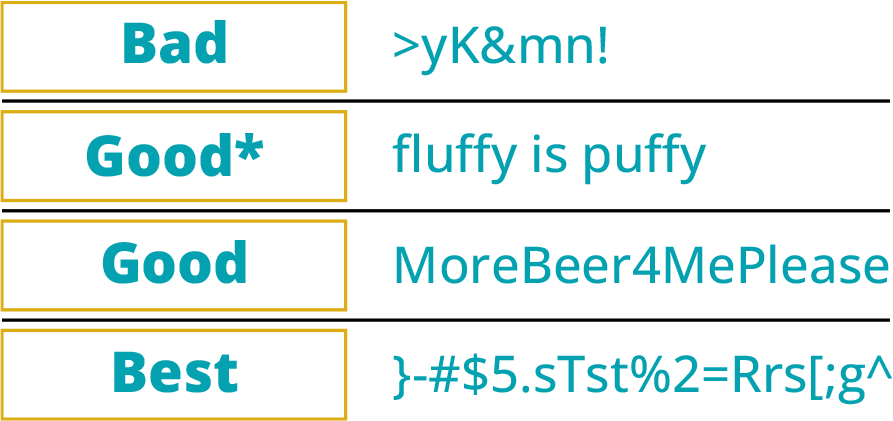
Password Best Practices
The biggest problem with passwords? Password reuse, and complexity is not nearly as useful as length at increasing security.
Mobile Device Management Policy
We can help you establish this with a few key rules:
You are prohibited from bringing company-owned mobile devices when traveling to high -risk locations (China, North Korea, etc.).
The circumvention of built-in security controls on mobile devices (e.g., jailbreaking or rooting) is strictly prohibited.
Only approved applications should be installed on mobile devices and the use of unapproved application stores is prohibited for company-owned mobile devices.
Call ICE Consulting today to learn more about our cybersecurity training.
A Track Record of Success and Industry Recognition

Top 10 Most Disruptive
Cloud Solutions Providers
CEOVIEWS MAGAZINE

Top 10 Managed Security
Service Provider
INSIGHTS MAGAZINE

Top 25 Life Sciences
Technology Vendors
CIO APPLICATIONS MAGAZINE

SOC 2 Certified
Less than 5% of MSPs have the prestigious SOC 2 Certification that helps ensure the security, confidentiality, and privacy of your company’s data.

24x7x365
Live monitoring, response, and support services—when and wherever you need it most.

97% Client Satisfaction Score
Based on more than 5,000 client reviews.

25 Years in Business
We have been providing Managed It services since 1997.
