Monitoring and Responding to Cybersecurity Threats and Vulnerabilities
24x7x365—SOCaaS
Security Operations Center-as-a-Service (SOCaaS) can shift your security posture away from one with only reactive responses to events to a proactive model with complete visibility into your IT environment as well as vulnerability management before breaches occur. This is critically important in today’s world. Over the last few years, security events have exploded both in numbers and scope.

Loss of intellectual property

Years of research data down the drain

Damage to your brand and reputation

Canceled business deals and partnerships

Millions in lost productivity, and legal/remediation expenses

Disclosure requirements imposed by your clients and governments intellectual property
$4.24 million
The average cost of one data breach in 2021
 $2.98 million
$2.98 million
Average total cost of a data breach for organizations with < 500 employees
Costs were consistently higher for organizations that lag in security automation and incident response processes
$180 per record
Customers’ personally identifiable information (PII) was the most frequently compromised type of record, and the costliest, in the data breaches studied
Source: The 2021 Annual Cost of a Data Breach Report, published by the Ponemon Institute and IBM Security. The research is conducted independently by Ponemon Institute, and the results are sponsored, analyzed, reported, and published by IBM Security.
And security breaches have continued to escalate during COVID-19.
Anti-Virus / Anti-Malware / EDR
Firewalls with UTM
URL & DNS Filtering Threat Detection / Threat Prevention IDS / IPS
Single Sign On / Multi Factor Authentication
Data encryption
Behavioral analytics
Threat Hunting
Email filter tuning and quarantine management
Servers & storage in data centers
Firewall/WAF, Servers on cloud infrastructure
Log Aggregation
Identify Access Management (IAM)
Hosted Email services
Penetration Testing
Wireless rogue activity detection
Monitoring of critical data flows
Threat intelligence feed analysis
“Experienced and knowledgeable” SOC teams are critical to ensure timely detection and effective security incident remediation.
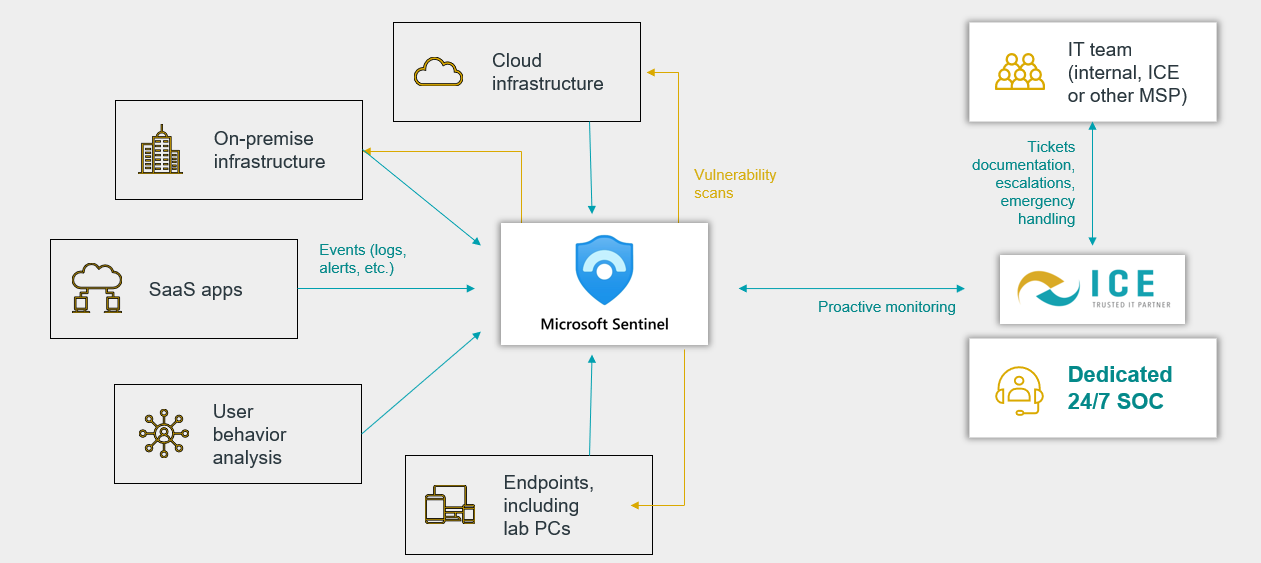
ICE’s SOC-AS-A-Service is The Answer

Provides 24/7/365, real-time visibility into your IT infrastructure





Monitor
Real-time monitoring of critical apps and services in a single dashboard
- Anti-Virus
- Encryption
- Firewalls
- Single Sign-on
- Multi-factor authentication
- Wireless Authentication
- Servers and Storage (Cloud or On-Prem)
- E-mail Services
- Cloud-Based Services
- Remote connections


Analyze
Centralized Log Collector to collect and store logs from services and devices for analysis. Risk management process that reduces chances of security breaches.


Respond
Respond immediately to cyber attacks to avoid security breach


Monitor
Incident Response Plan (IRP)
An Industry-Leading Partnership
We have partnered with Microsoft—Microsfot’s SIEM Platform Sentinel was named a leader in the 2022 Gartner Critical Capabilities for SIEM (for Security Information and Event Management).
What are the top 10 types of security breaches?
- Activity by a terminated user
- Excessive privileges
- Outbound connect to a black site
- Inbound connection from black site
- Unusual activity in the application (data snooping)
- Unusual activity in the application (peer anomaly—unusual compared to peer)
- Unusual activity in the application (user anomaly—never before seen activity)
- Unusual source—possible compromise
- Repeat failed logins followed by login success—source IP or destination user (hacker)
- Unusual process started
ICE is a Top 10 Managed Security Provider


SOC 2 Certified
Less than 5% of MSPs have the prestigious SOC 2 Certification that helps ensure the security, confidentiality, and privacy of your company’s data.

24x7x365
Live monitoring, response, and support services—when and wherever you need it most.

97% Client Satisfaction Score
Based on more than 5,000 client reviews.

25 Years in Business
We have been providing Managed It services since 1997.


 $2.98 million
$2.98 million
