Designed for Fast-growing Enterprises—Startups and Mid-sized Firms

Like most growing businesses, you need to focus on your core business and often don’t have time or the technical expertise required to commit to managing your IT infrastructure and security needs. Also, it is very costly and may not make sense to develop your own IT department. ICE Consulting can help.
Since 1997, we’ve worked with more than 500 client firms in a wide variety of industries including technology, biotech and life sciences, financial services, education, nonprofit, legal, and manufacturing. We know how to build custom IT solutions from the ground up and how to manage your IT infrastructure efficiently and effectively.
ICE is Your IT Department
If you’re a mid-sized firm and need to focus on your core business, we can function as your internal IT department. Once fully embedded into your organization, we can provide complete end-to-end managed IT services:
IT STRATEGIC SERVICES
- Provide IT Director services
- Design IT Infrastructure On-Premise and Cloud
- Implement Process & Procedures based on IT best practices
- Meet compliance requirements
- Handle office build-out, migration & expansions
IT SUPPORT SERVICES
- Onsite technical services
- Helpdesk-live tech support 24x7x365 including holidays
- Proactive weekly Preventive Maintenance:
- Network Security-Network Infrastructure
- Systems Infrastructure
- Endpoints (Desktops, Laptops & Mobile devices)
- NOC (Network Operation Center) 24x7x365 . Provide IT training to users
IT TECHNICAL SERVICES
- Firewall, Switching & Routing
- Linux, Windows & Mac servers & systems
- Cybersecurity
- Design & implement Zero Trust Network
- Virtualization & Storage
- Backup & Disaster Recovery
- Wireless solutions
- Single sign on (SSO) & Multifactor Authentication
- Mobile Device Management (MDM)
- Cloud Services Management
- Onboarding & offboarding employees & contractors
- Printing & phone services
IT ADMINISTRATIVE SERVICES
- Regular IT meeting
- Project Management
- Ticket Management
- Client Satisfaction Reporting
- Weekly & Monthly IT Reporting
- Key Performance Indicators (KPI) Reporting
- Hardware & Software procurement
- Asset Management
- Vendor Management
- Cabling services
- IT Room, Cooling, HVAC
- IT Documentation
We Customize Pricing to Meet Your
Business Needs and Budget
We understand that every business has different needs and budget requirements. If you’re a startup, you may need to focus on research and product development and if you are a mid-sized firm, you may need to focus on customer acquisition and marketing. We don’t believe in one-size-fits-all solutions. We customize our IT services to meet and exceed your IT needs and requirements and your budget.
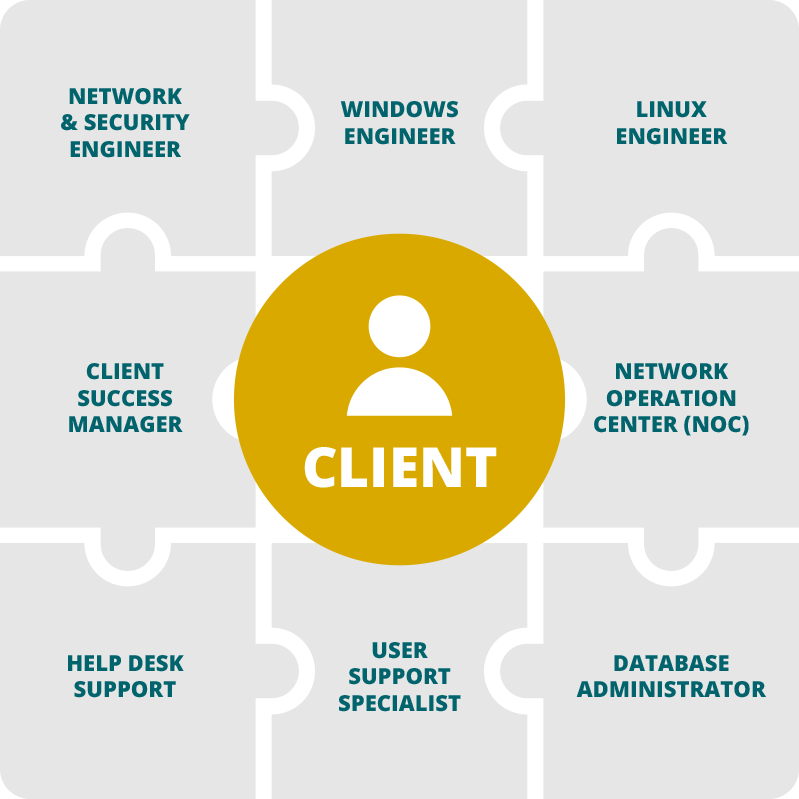
We Assign Specialized Engineers to
Every Client
One of the many ways we are different from our competitors is our approach to assigning specialized engineers to every client team. We hire and train specialists in a particular field, not the generalists you may find with our competitors. We carve out time and assign primary and secondary engineers to our client teams from each of the following departments. These engineers will work with you to design, implement, and manage IT infrastructures in the best possible way.
- Network Engineering Department
- Security Engineering Department
- Systems & Cloud Engineering Department
- User Support Department
- Helpdesk Department
- NOC Department
- SOC Department
- Database Department
- Client Success Manager
In addition, we offer:
- Helpdesk Services 24x7x365 by a Live ICE Tech Support Employee.
- NOC (Network Operation Center) services includes 24x7x365 IT infrastructure Monitoring and response services.
- SOC (Security Operation Center) services includes 24x7x365 complete IT infrastructure Security Monitoring and Response services with Securonix SIEM
Testimonial
“ICE designed our infrastructure when we were only a 20-employee company. As our business has grown—we now employ over a hundred people—ICE has been able to grow and manage our IT infrastructure with no trouble.”
– Vice President, Finance & Operations, Biotech Company
Innovative Biotech Company Hires ICE to
Scale and Secure IT Infrastructure
A Track Record of Success and Industry Recognition

Top 10 Most Disruptive
Cloud Solutions Providers
CEOVIEWS MAGAZINE

Top 10 Managed Security
Service Provider
INSIGHTS MAGAZINE

Top 25 Life Sciences
Technology Vendors
CIO APPLICATIONS MAGAZINE

SOC 2 Certified
Less than 5% of MSPs have the prestigious SOC 2 Certification that helps ensure the security, confidentiality, and privacy of your company’s data.

24x7x365
Live monitoring, response, and support services—when and wherever you need it most.

97% Client Satisfaction Score
Based on more than 5,000 client reviews.

25 Years in Business
We have been providing Managed It services since 1997.
