End-to-end Managed IT Services
IT Support so you can focus on growing your business
Our Managed Services take the headache out of managing IT and give you the peace of mind you need to focus on your core business. With our proactive management and monitoring, we’ll ensure that your network, systems, and endpoints are secured and stay up and running, and we’ll make fire drills a thing of the past. We’ll increase your IT security, simplify IT management, and create a sustainable environment at a cost often less that you are already spending for IT services.

Proactive IT Services
We perform PROACTIVE IT services. We have developed a proprietary IT checklist for proactive IT maintenance for:


Systems Infrastructure

Network Infrastructure

Security

End-Point systems

Transparent IT Services
We provide weekly and monthly reports on:

Network Infrastructure
Ticket analysis and trending

KPI (Key Performance Indicators)

Client Satisfaction Report

Executive Summary

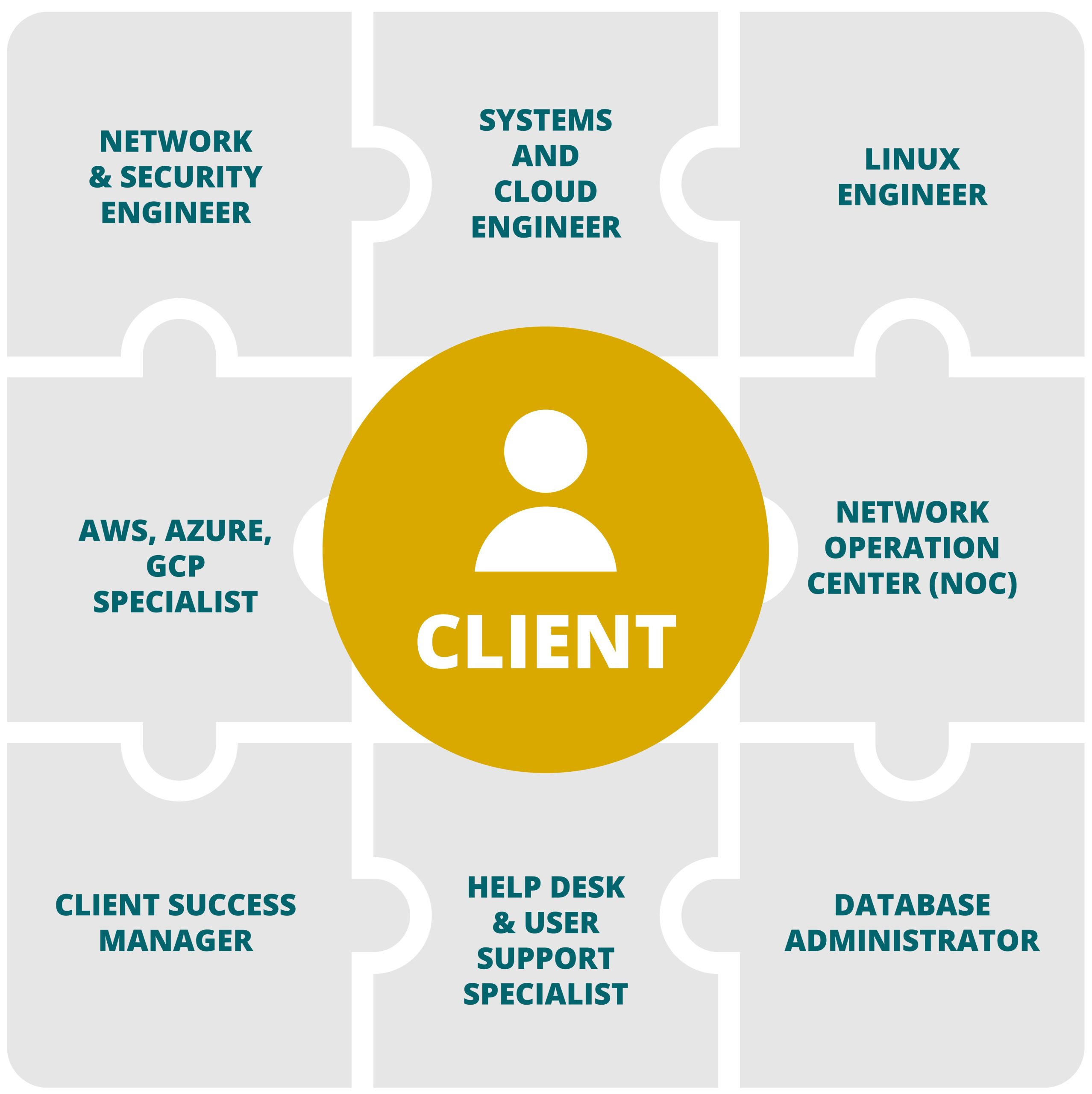
Specialized team of engineers
We have a team of specialized engineers assigned to every client—and all our departments are managed by seasoned professionals and technical leads with 20+ years of experience. Unlike our competitors, we train ICE engineers to be specialists in a particular field. Instead of having an IT generalist who may NOT have the detailed expertise your business requires, we ensure our team knows your business, industry, and requirements.
Technical Team Assigned To Client
Make Us Part of Your IT Department
As a managed IT service provider, we will work as your “IT Department” but at the fraction of the cost of having your own internal IT department. We’ll increase your IT security, simplify IT management, and create a sustainable environment at a cost often less that you are already spending for IT services.
Our services include:
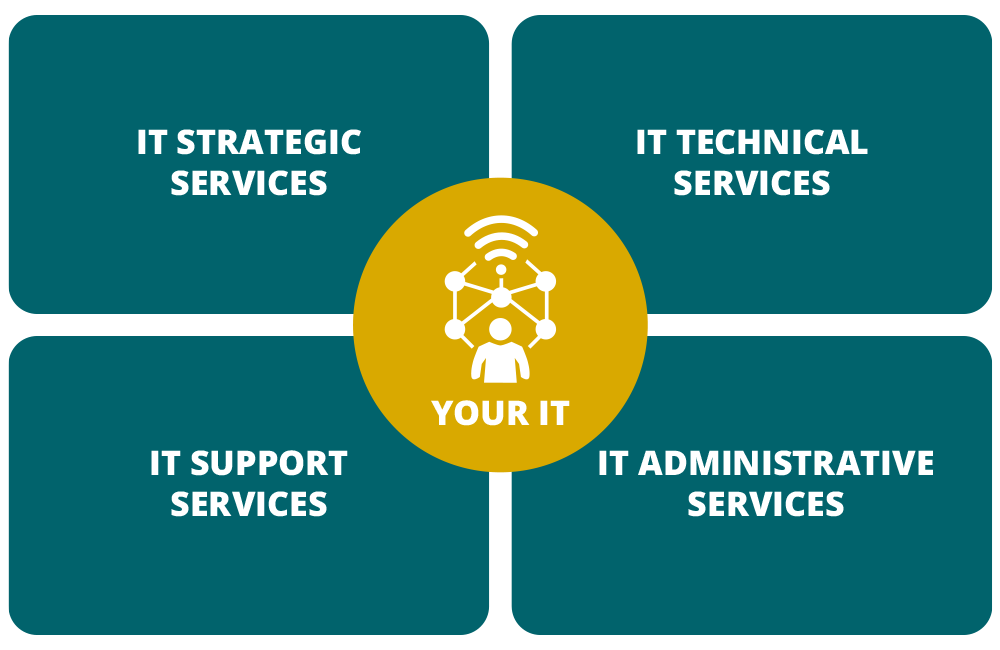
IT STRATEGIC SERVICES
- Provide IT Director services
- Design IT Infrastructure On-Premise and Cloud
- Implement Process & Procedures based on IT best practices
- Meet compliance requirements
- Handle office build-out, migration & expansions
IT SUPPORT SERVICES
- Onsite technical services
- Helpdesk-live tech support 24x7x365 including holidays
- Proactive weekly Preventive Maintenance:
- Network Security -Network Infrastructure
- Systems Infrastructure
- Endpoints (Desktops, Laptops & Mobile devices, Lab devices, Lab computers)
- NOC (Network Operation Center) 24x7x365 5. Provide IT training to users
IT TECHNICAL SERVICES
- Firewall, Switching & Routing
- Linux, Windows & Mac servers & systems
- Cybersecurity
- Design & implement Zero Trust Network
- Virtualization & Storage
- Backup & Disaster Recovery
- Wireless solutions
- Single sign on (SSO) & Multifactor Authentication
- Mobile Device Management (MDM)
- Cloud services management
- Onboarding & offboarding employees & contractors
- Printing & phone services
IT ADMINISTRATIVE SERVICES
- Regular IT meeting
- Project Management
- Ticket Management
- Client Satisfaction Reporting
- Weekly & Monthly IT Reporting
- Key Performance Indicators (KPI) Reporting
- Hardware & Software procurement
- Asset Management
- Vendor management
- Cabling services
- IT Room, Cooling, HVAC
- IT Documentation
Testimonial
“As a growing biotech company, our company has been using ICE Consulting exclusively for the past 4 years and I am very happy with their solutions and support. ICE has helped us design and implement a robust IT infrastructure as our company grew from 20 employees to 200+ employees and are currently maintaining the existing systems. We trust ICE Consulting and they have always been very prompt in addressing our needs and requirements. Their staff of Windows, Linux, Network engineers, and DBAs are very helpful and knowledgeable with the products that they support. I would highly recommend ICE for providing quality services and to reduce the overall costs of supporting and maintaining the IT infrastructure.”
– Senior Director, Information Technology, Stemcentrex (now AbbVie):
Innovative Biotech Company Hires ICE to
Scale and Secure IT Infrastructure
A Track Record of Success and Industry Recognition

Top 10 Most Disruptive
Cloud Solutions Providers
CEOVIEWS MAGAZINE

Top 10 Managed Security
Service Provider
INSIGHTS MAGAZINE

Top 25 Life Sciences
Technology Vendors
CIO APPLICATIONS MAGAZINE

SOC 2 Certified
Less than 5% of MSPs have the prestigious SOC 2 Certification that helps ensure the security, confidentiality, and privacy of your company’s data.

24x7x365
Live monitoring, response, and support services—when and wherever you need it most.

97% Client Satisfaction Score
Based on more than 5,000 client reviews.

25 Years in Business
We have been providing Managed It services since 1997.
